
Enterprise networks, built from the ground up
Get a demo
Full-stack networks.
Internet, Wired, Wi-Fi, and Cellular.
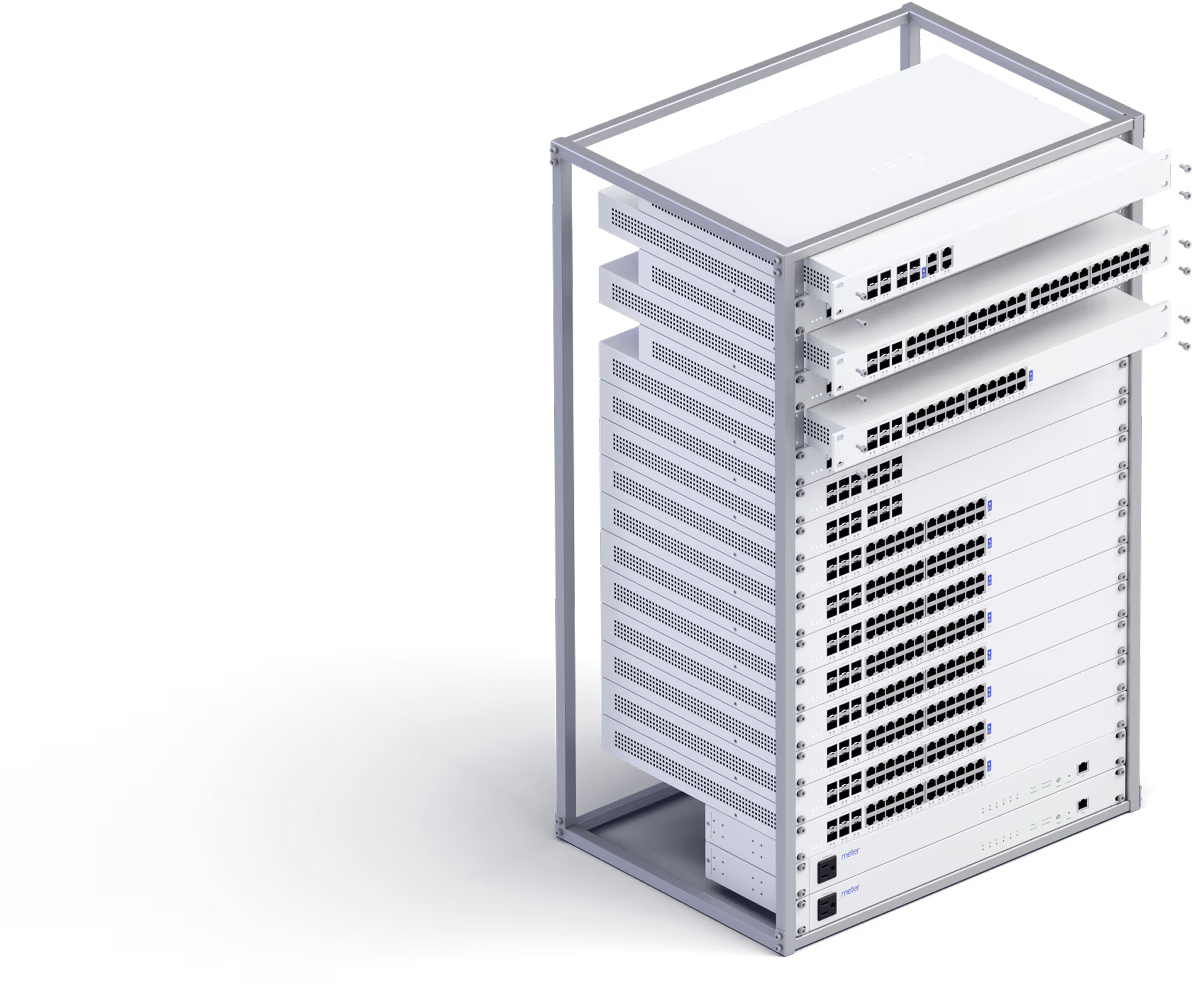
Hardware designed and manufactured by Meter
Networks built the way they should be, from the ground up.
Use Meter to ensure your enterprise networks have the best performance, security, and reliability.
Install to refresh
Meter is software-led across install, support, and lifecycle management. Work with Meter or our partners across the globe for optimized design, deployment, and maintenance.
Installation process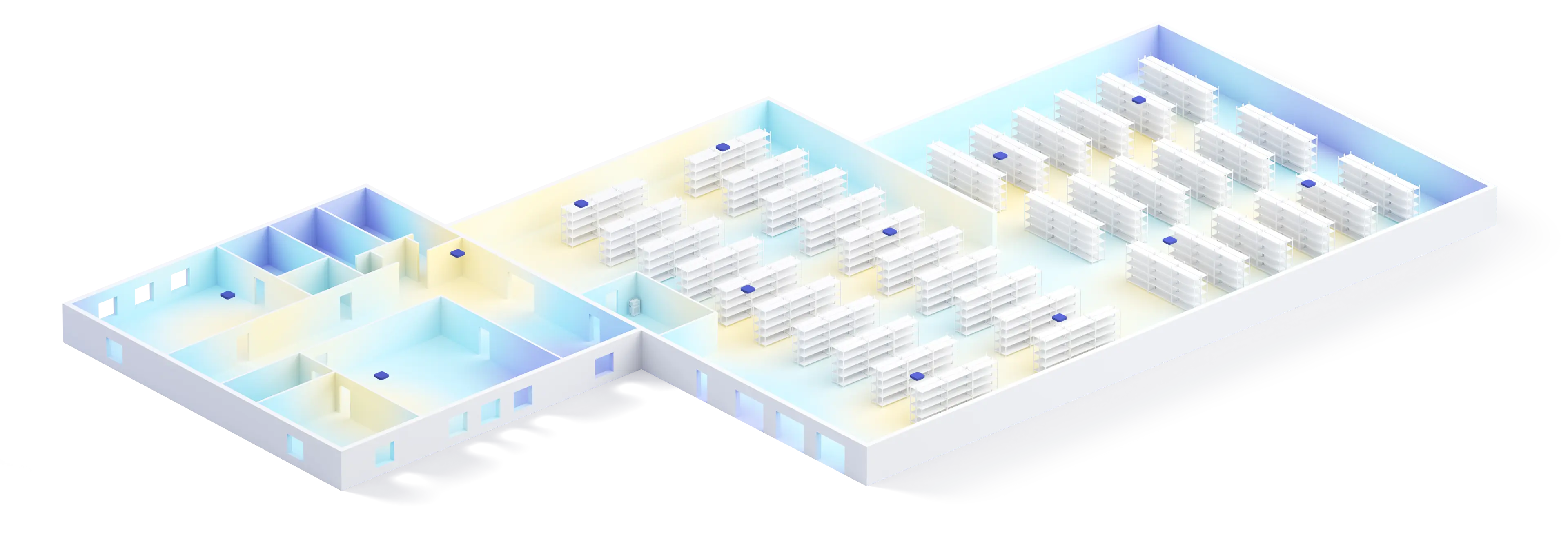
Intuitive software packed with enterprise controls
Get deep visibility and control with our dashboard or use Command to generate one for your unique workflow.
Configurability
Security
Visibility
Resiliency
Custom dashboard
Generated UI
Auto-filled
SSID
Globex
Authentication
WPA2
surface1-blur4-5
Rate limit rule
Globex bandwidth control
Download limit
100Mbps
Upload limit
Mbps
Bindings
VLAN
private
Firewalls
2/2 online
Switches
1
71/72 online
Access points
121/121 online
PDUs
24/24 online
ISP throughput
100 Gbps50 Gbps0 Gbps
7:35 PM3:35 AM11:35 AM
Now
Built to scale
Companies of all sizes use Meter. Our hardware and software scale with multi-site management, handling thousands of locations and millions of devices.

Trusted by technology and networking leaders everywhere
Customer storiesWhen we first started looking into how we could scale across the country, we knew we needed a partner that could help us with networking. Moving across several different states, with different locations, the company was growing quickly and networking as a service was going to be a requirement.
Codi HandleyDirector of Security & IT